
Introduction
In my servers, I usually encrypt all partitions and entire disk using Linux Unified Key Setup-on-disk-format (LUKS) for security and privacy reasons. When it’s a Root FileSystem, I can unlock the LUKS-protected partition by providing a passphrase at boot time. You must be in front of your computer or use a remote console to open the encrypted disk under Linux at boot time. However, if your system is not local, you won’t be able to unlock and boot your Linux box. We can use the Dropbear SSH server for LUKS-encrypted Debian, Ubuntu, or any other Linux distro via SSH to solve this problem. Let us see how to unlock LUKS using Dropbear SSH keys in Linux at boot time.
I have full-disk encryption on my server. This meant setting up LUKS. Actual setup of encryption is outside of the scope of this document. A consequence of full system encryption is that you need to type in your system passphrase each time you power on your computer.
We can use the Dropbear SSH server for LUKS-encrypted Debian, Ubuntu, or any other Linux distro via SSH to unlock an encrypted root file system
Using Dropbear, it’s possible to enter the password remotely during the boot process. The trick involves embedding a small ssh server (dropbear) in the initramfs that allows you to enter the password remotely for the root partition at boot time.
NOTE It’s important to use dropbear-initramfs, not just dropbear
First some Theory on how the unlocking works
The service that unlocks the root filesystem is generally not a traditional systemd service but part of the initramfs process. The unlocking is handled by cryptsetup and integrated into the boot process via initramfs, where it prompts for a passphrase or retrieves a key to unlock the root partition before handing control over to systemd.
The service that handles unlocking the root filesystem on Linux systems when it is encrypted (typically with LUKS) is integrated into the initramfs system. Specifically, the relevant components and processes are:
1. cryptsetup Integration in Initramfs
When the root filesystem is encrypted using LUKS, the boot process involves an early userspace environment called initramfs (initial RAM filesystem). Inside this environment, the system uses cryptsetup (or related utilities) to unlock the encrypted root partition before transitioning to the actual root filesystem.
The service or process that manages unlocking the root filesystem in this early stage is typically integrated into the initramfs and doesn’t rely on traditional systemd services at that point because systemd has not yet fully started.
2. Key Components for Unlocking Root Filesystem
cryptsetup: This tool is responsible for unlocking the LUKS-encrypted partition./etc/crypttab: This file defines encrypted block devices that need to be unlocked. It can specify which device to unlock and how to unlock it (e.g., using a passphrase, keyfile, or hardware security module).dracutorinitramfs-tools: These tools generate the initramfs image, which containscryptsetupand other necessary utilities for unlocking the root filesystem during early boot.systemd-cryptsetup: Insystemd-based systems, oncesystemdstarts during the boot process, it might manage the encrypted partitions usingsystemd-cryptsetupservice for non-root encrypted filesystems. However, the root filesystem is generally handled within the initramfs.
3. Unlocking Process During Boot
The process typically follows these steps:
-
Kernel Loads Initramfs: When the system boots, the Linux kernel loads the initramfs image into memory, which contains a minimal environment needed to mount the root filesystem.
-
cryptsetupin Initramfs: Inside this environment,cryptsetupis used to prompt for a passphrase or retrieve a key to unlock the encrypted root partition. -
Mounting the Root Filesystem: After successfully unlocking the root partition, it is mounted, and the boot process proceeds to transition to the full root filesystem.
-
Handing Off to
systemd: Once the root filesystem is unlocked and mounted, the system hands control over tosystemd, which continues booting the rest of the system.
4. Configuring the Unlocking Process
-
/etc/crypttab: This file can be used to specify the encrypted partitions that need to be unlocked during boot. For the root partition, this is typically handled by the initramfs, but for other encrypted partitions, it might look something like this:root_encrypted UUID=your-root-partition-uuid none luksroot_encrypted: The name of the mapping (used bycryptsetup).UUID=your-root-partition-uuid: The UUID of the encrypted device.none: Indicates that no keyfile is being used (a passphrase will be prompted for).luks: Specifies that LUKS encryption is being used.
-
Initramfs Configuration: Depending on your distribution, the process of configuring initramfs to unlock the root partition is handled by tools like
initramfs-tools(on Debian/Ubuntu) ordracut(on Fedora/Red Hat/CentOS). These tools ensure thatcryptsetupis included in the initramfs image and can prompt for the passphrase during boot.
5. Remote Unlocking of Root Filesystem
In systems where remote unlocking of the root filesystem is needed (such as headless servers), a service like Dropbear or a similar SSH server is embedded into the initramfs. This allows you to SSH into the early boot environment and provide the LUKS passphrase remotely.
The process typically involves:
- Embedding a minimal SSH server (like Dropbear) in the initramfs.
- SSH-ing into the system during boot and providing the passphrase to unlock the root filesystem.
6. systemd Services Related to Cryptsetup
Once the root filesystem is unlocked and the system has fully booted, systemd manages other encrypted partitions using the systemd-cryptsetup@.service. This service is responsible for managing LUKS devices that are defined in /etc/crypttab.
For example, if you have additional encrypted filesystems (besides the root filesystem), systemd will manage them via this service:
systemctl status systemd-cryptsetup@<device-name>
What is the Dropbear SSH server?
Dropbear is a free and open-source SSH server created explicitly for embedded Linux and Unix systems with low resource requirements. It implements version 2 of the Secure Shell (SSH) protocol. It supports RSA and elliptic curve cryptography for key exchange. Dropbear is compatible with OpenSSH ~/.ssh/authorized_keys public key authentication. I am assuming that you already installed Debian or Ubuntu Linux with LVM and LUKS
Identity Encrypted Partitions
We can also use the cat command (or use the bat command if you want to see fancy outputs) to identity encrypted partitions:
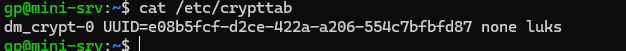
sudo cat /etc/crypttab
Here is what I see:
dm_crypt-0 UUID=e08b5fcf-d2ce-422a-a206-554c7bfbfd87 none luks
Step 1. First: Configure GRUB
You may ignore this step, if GRUB is already configured to have network on boot. Otherwise you have to configure it to use DHCP or a static IP. IMPORTANT If you setup GRUB with DHCP, you need to have your router reserve an ipaddress for your server and always give the same IP, so it’s like you have a static IP address. Why ? Because, you want to connect to your server remotely, you need his IP address! If it changes, you are in trouble! I personally have my router setup to give the same IP address (reserved) to my server.
For Static IP, specify the IP configuration at the Kernel boot line. To do this edit the file /etc/default/grub and define the line:
GRUB_CMDLINE_LINUX="ip=<client-ip>:<server-ip>:<gw-ip>:<netmask>:<hostname>:<device>:<autoconf>"
If your server gets the IP address automatically (DHCP)
GRUB_CMDLINE_LINUX="ip=dhcp"
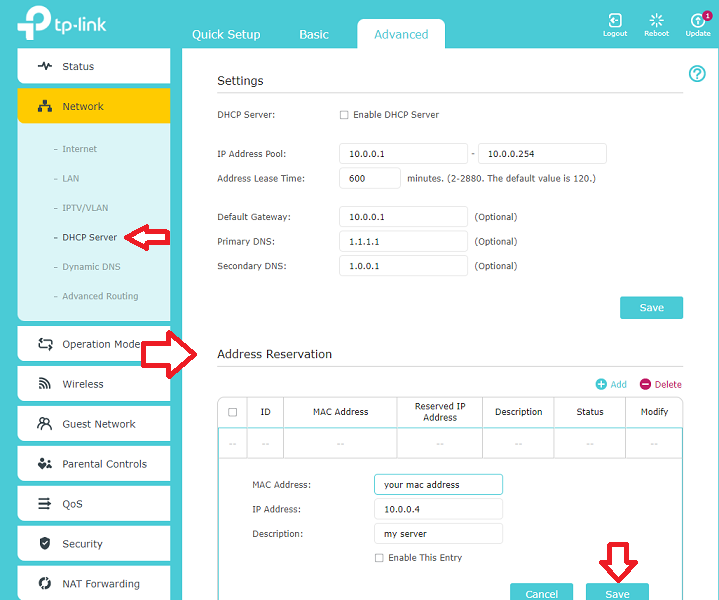
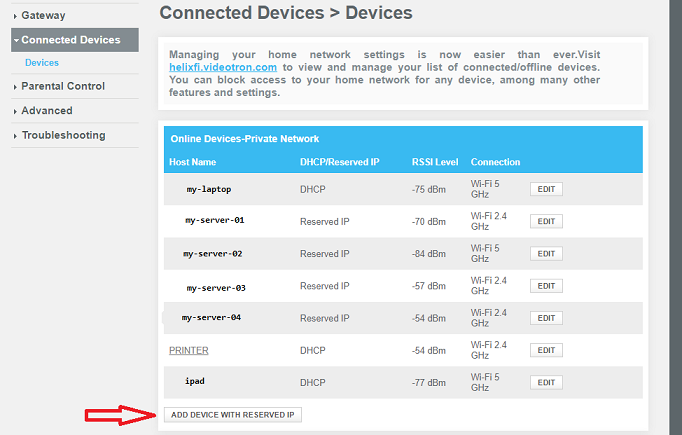
To configure your router to give a static IP , log in to the router interface, when you boot the server with GRUB ni DHCP, wait for it to send the DHCP request, then check the router logs and interface.
Below are 2 examples of router interfaces to configure the DHCP address reservations:
tp link
milestrong
Using the format specified in the file Documentation/nfsroot.txt of the Linux kernel documentation. For example: GRUB_CMDLINE_LINUX=”ip=192.168.122.192::192.168.122.1:255.255.255.0::eth0:none”
Reload the grub configuration
update-grub
Step 2. Install dropbear and busybox
During the installation, I get a warning about dropbear: WARNING: Invalid authorized_keys file, remote unlocking of cryptroot via SSH won’t work!, and I was not able to find the needed keys.
First make sure that initramfs-conf busybox and dropbear-initramfs are installed
sudo apt-get install initramfs-conf dropbear-initramfs busybox
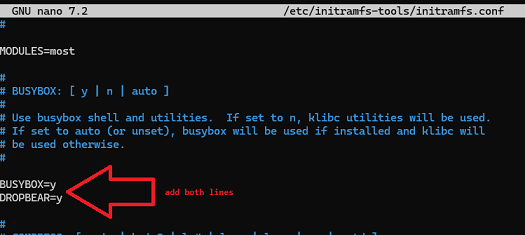
Step 3. Activate BUSYBOX and DROPBEAR in initramfs
sudo nano /etc/initramfs-tools/initramfs.conf
Add these:
BUSYBOX=y
DROPBEAR=y
Also make sure this is done:
sudo mkdir /etc/initramfs-tools/root
sudo mkdir /etc/initramfs-tools/root/.ssh
sudo cp dropbear_* /etc/initramfs-tools/root/.ssh/
sudo cp id_* /etc/initramfs-tools/root/.ssh/
sudo cp authorized_keys /etc/initramfs-tools/root/.ssh/
Step 3. Generate our keys
For this, we rely on dropbear, by passing the -R argument:
sudo nano dropbear -p 2222 -R -F
Step 4. Set dropbear to start
sudo nano sudo nano /etc/default/dropbear
Change NO_START=1 to NO_START=0
Step 5 KEYS
Add your public key (most of the time ~/.ssh/id_rsa.pub) in the file /etc/dropbear-initramfs/authorized_keys.
To create a key (in dropbear format):
dropbearkey -t rsa -f /etc/initramfs-tools/root/.ssh/id_rsa.dropbear
To convert the key from dropbear format to openssh format:
/usr/lib/dropbear/dropbearconvert dropbear openssh \
/etc/initramfs-tools/root/.ssh/id_rsa.dropbear \
/etc/initramfs-tools/root/.ssh/id_rsa
To extract the public key:
dropbearkey -y -f /etc/initramfs-tools/root/.ssh/id_rsa.dropbear | \
grep "^ssh-rsa " > /etc/initramfs-tools/root/.ssh/id_rsa.pub
To add the public key to the authorized_keys file:
cat /etc/initramfs-tools/root/.ssh/id_rsa.pub >> /etc/initramfs-tools/root/.ssh/authorized_keys
update-initramfs -u
Unlocking
Note, if you want to avoid to have clash between the keys between dropbear and openssh (they share the same ip, but use a different key), you may want to put in your client ~/.ssh/config something like that:
Host myserver_luks_unlock
User root
Hostname <myserver>
# The next line is useful to avoid ssh conflict with IP
HostKeyAlias <myserver>_luks_unlock
Port 22
PreferredAuthentications publickey
IdentityFile ~/.ssh/id_rsa
To unlock from remote, you could do something like this:
ssh -o "UserKnownHostsFile=~/.ssh/known_hosts.initramfs" \
-i "~/id_rsa.initramfs" root@initramfshost.example.com \
"echo -ne \"secret\" >/lib/cryptsetup/passfifo"
Here’s a Powershell Script to unlock the server from a Windows machine
function Unblock-MiniSrvRootFs {
[CmdletBinding(SupportsShouldProcess)]
param(
[Parameter(Mandatory=$false)]
[String]$ServerIp = "10.0.0.111"
)
try{
$IsConnected = $False
Write-Host "Waiting for minisrv ($ServerIp) to be up..." -NoNewLine
While($IsConnected -eq $False){
Start-Sleep 1
Write-Host ". " -NoNewLine
$IsConnected = Test-Connection -TargetName "$ServerIp" -Ping -IPv4 -Count 1 -TimeoutSeconds 1 -Quiet -ErrorAction Ignore
}
Write-Host "`nok!"
$SshExe = (Get-Command 'ssh.exe').Source
$Credz = Get-AppCredentials -Id "minisrv.initramfs"
if($Null -eq $Credz){ throw "no credentials found!" }
$Username = $Credz.UserName
$Password = $Credz.GetNetworkCredential().Password
$SshArg = '{0}@{1}' -f $Username, $ServerIp
$Cmd = 'echo -ne "{0}" >/lib/cryptsetup/passfifo' -f $Password
&"$SshExe" '-o' "UserKnownHostsFile=~/.ssh/known_hosts.initramfs" "$SshArg" "$Cmd"
}catch{
Write-Host "$_" -f DarkRed
}
}
Also Here’s a script that may be usefull to you.
Sources
- Unlocking a LUKS encrypted root partition remotely via SSH
- How do I get dropbear to actually work with initramfs
- Remote unlocking LUKS encrypted LVM using Dropbear SSH in Ubuntu Server 14.04.1
- SSH to decrypt encrypted LVM during headless server boot?
