
OpenVPN Interceptor - To use Freedome with any OpenVPN client
F-Secure’s Freedome VPN is notoriously locked down—no native Linux support, tightly bundled client… I jailbroke it so I can use it with raw OpenVPN configs using some light magick.
OpenVPN Interceptor - To use Freedome with any OpenVPN client
Preparation
Prerequisites you must download and install:
- Download Wireshark and install it
- My memory search tool: mseek, that you can compile.
- Extract your client cert
client.crtand keyclient.key(check C:\ProgramData\F-Secure\FSVpnSDK\keys as administrator), make copies as backup, and keep working copies somewhere else. - Extract the x1.crt file from C:\ProgramData\F-Secure
Get the private key password
- Run Freedome, log in with your account, connect to the VPN
- Open a PowerShell Console, get the PID of openvpn.exe 1
- Then run
NETSTAT.EXE -aon | findstr <PID HERE>to get the local port openvpn is connected to.2 - Open WireShark and set the filter to the port openvpn.exe is using 3
- Reconnect and disconnect from the VPN
- Analyse the capture, see thet openvpn.exe is used with -stdin and management mode 4
- you will see the private key. 5
F-Secure Fights back!
Fsecure VPN works internally using the management console. FSVpnSDK sends command to openvpn.exe to setup the VPN. In order to fight against some people using a stub replacing the openvpn.exe, they added a check for the openvpn.exe digital signature, so one cannot replace the openvpn.exe to dump the commands sent to it. Also, they added a second layer of encyption to the private key using a proprietary algorithm (C:\ProgramData\F-Secure\FSVpnSDK\keys\client.key).
Using the openvpn.exe stub
In the latest version, FSVpnSDK checks the openvpn.exe digital signature so this wont work anymore
Compile the projectRun scripts/install.ps1, it will replace the openvpn.exe after making a backupRun Freedome, log in with your account, connect to the VPNGet your dumped config
💡 Advanced - Get Private Key #1
Because your private key is NOT ONLY encrypted using DES, but DOUBLY ENCRYPTED on disk using a proprietary algorithm so you cannot using it as-is with openvpn.exe. We need to get the clear version of the encrypted-base64 key we can use. The latter will then be decrypted using the password we got in wireshark 5
Having not idea how to decrypt it, I was trying to generate errors to get meaningful logs.
- Disconect VPN, and break and invalidate my key 7
- Monitor log files, check for ERROR, Warning, etc… 8
- Reconnect VPN, waitin… BOUM! Good hint! The code looks for a string
"</key>"in the decrypted text - Set the good key back using the backup we did earlier 9
Now we know the CLEAR TEXT of the Private Key has </key> Lets look in memory for it.
💡 Advanced - Get Private Key #2
To do this, you need my memory search tool mseek
- Search for a string in a specific process 10
- Search for a string in a specific process, print data around found instance 11
- Search for a string in a specific process, print data around found instance 12
- Get the size of data between 2 points 13
- Dump only printable text around matches and write to file 14
- Fix key format 15
List VPN using scripts
use scripts/Get-FSecureSiteList.ps1
Example configuration
If you have your private key, password, the CA cert already and the gateway you wish then you can replace values here .. code-block:
Important: comment out ; pull-filter ignore redirect-gateway That means the server does tell the client to redirect the traffic, but the client is still explicitly configured to ignore this push.
<ca>
CERTIFICATE HERE
</ca>
<key>
PRIVATE KEY HERE
</key>
cert <cert path here>
verb 4
client
dev tun
suppress-timestamps
preresolve
route-delay 0 12
push-peer-info
setenv UV_CLP peerid:2
replay-window 512 15
tcp-queue-limit 128
nobind
float
resolv-retry 20
server-poll-timeout 10
persist-key
mute-replay-warnings
remote-cert-tls server
data-ciphers AES-256-GCM:AES-128-GCM:AES-256-CBC
; comp-lzo
allow-compression no
cipher AES-256-CBC
auth SHA256
; pull-filter ignore redirect-gateway
<connection>
fragment 1400
remote freedome-ca-montreal.freedome-vpn.net 2747
proto udp
explicit-exit-notify 1
</connection>
<connection>
remote freedome-ca-montreal.freedome-vpn.net 443
proto tcp-client
</connection>
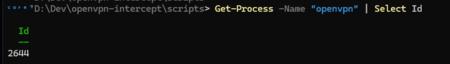 [1]
[1]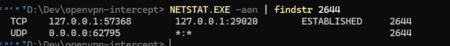 [2]
[2]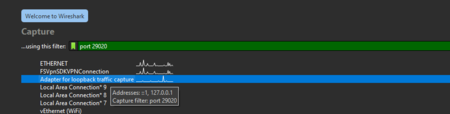 [3]
[3]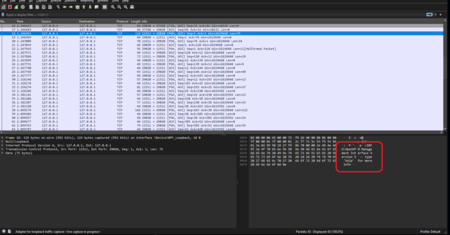 [4]
[4]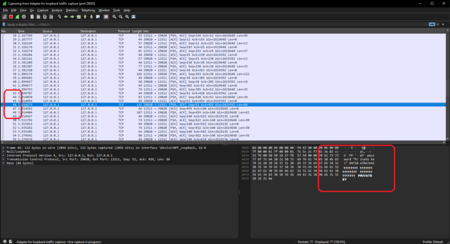 [5]
[5]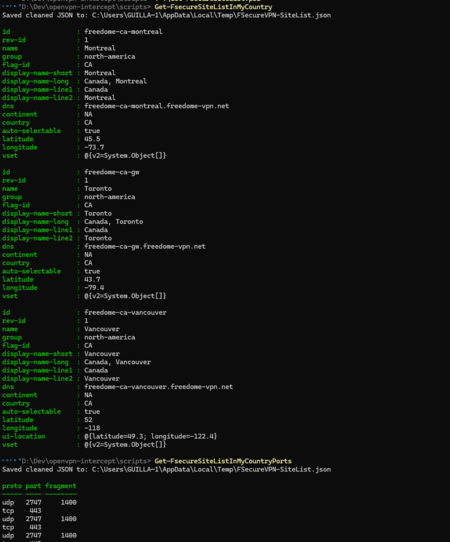 [6]
[6] [7]
[7]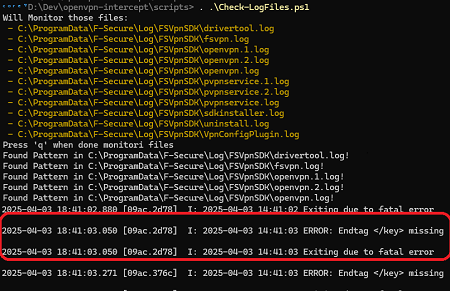 [8]
[8] [9]
[9]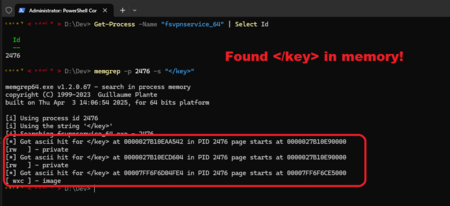 [10]
[10]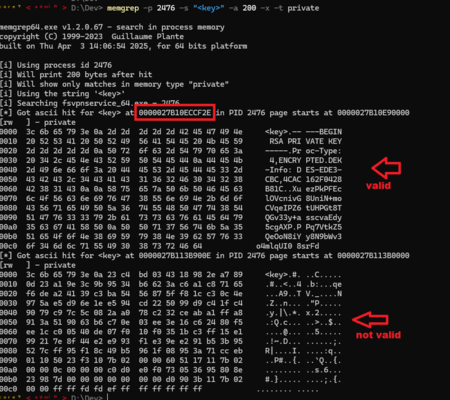 [11]
[11]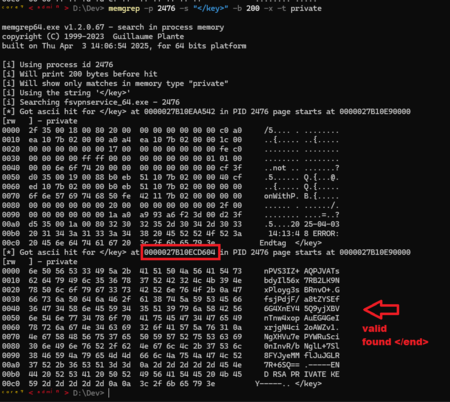 [12]
[12]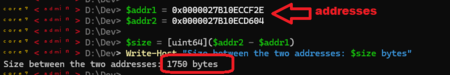 [13]
[13]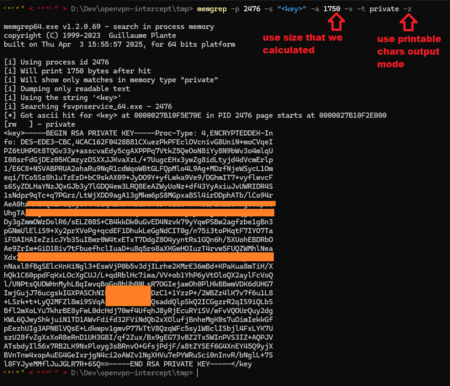 [14]
[14]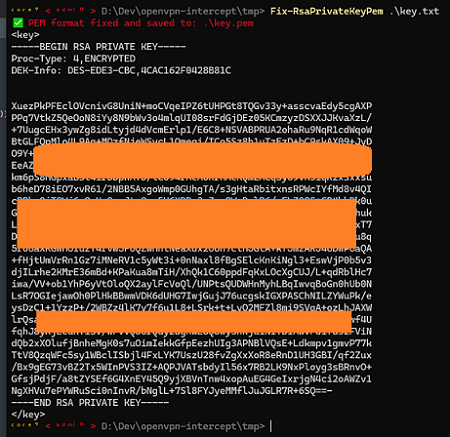 [15]
[15]